Table of Contents
Hello, in this article I will go more than authentication, numerous procedures to implement it, each individual of their drawbacks, and which a single you might want to use! Let us get started out!
What is Authentication?
Authentication or auth for brief is the approach exactly where a server recognizes the id of a person. Authorization is then completed, to allocate a role to the authenticated consumer and allocate the required expert services to that particular consumer.
There are 2 ways you can put into action auth:
Let’s choose a deep dive into periods!
Sessions
Server-facet classes had been the regular way to implement auth. The circulation of a session can be illustrated like this:
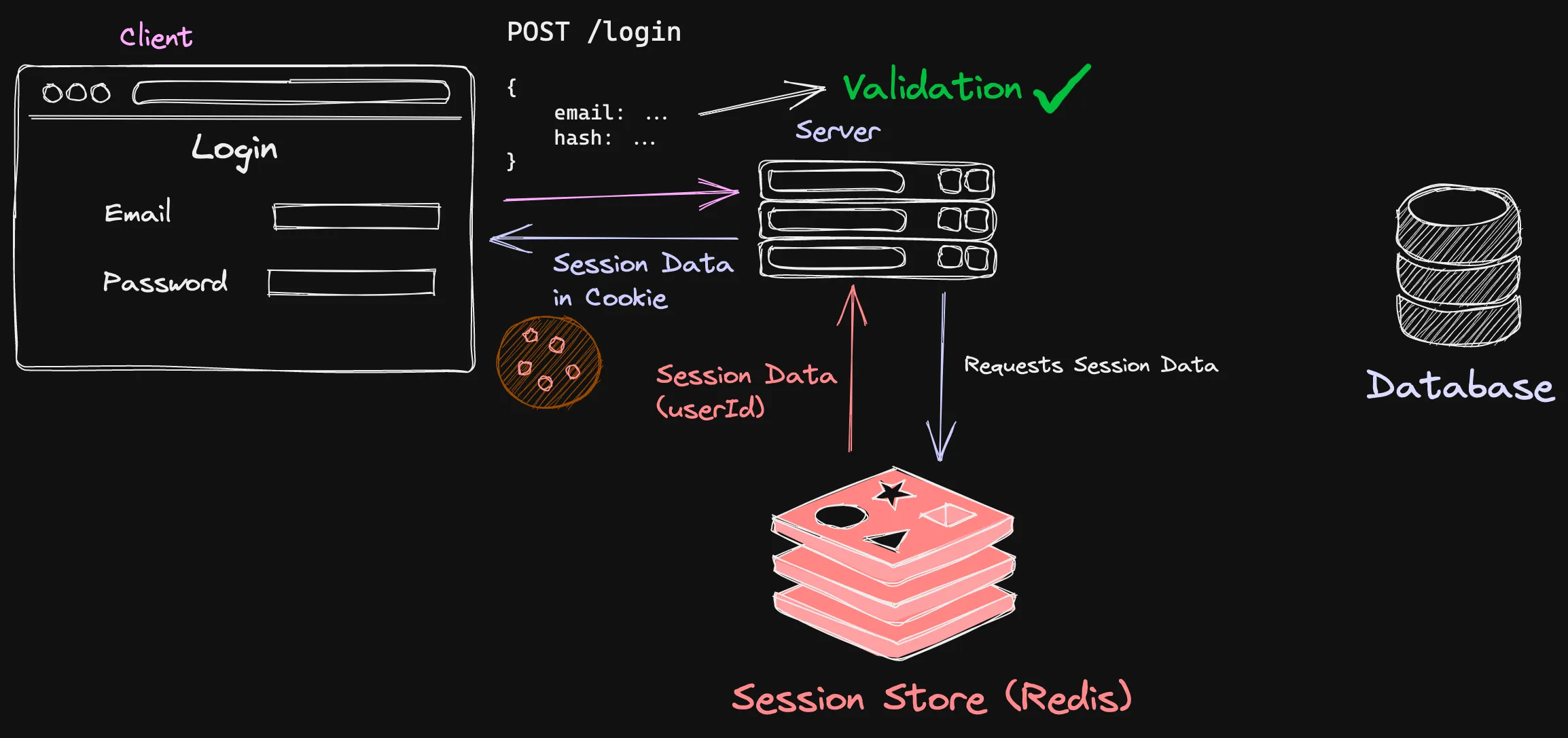
The procedure begins with the client:
- Receiving an e-mail and a password
- Then, hashing the password
- And sending the e-mail and the hashed password to the server
Hashing is the course of action of scrambling a value using a critical that is despatched to an algorithm. Hashed values can not be decrypted! Argon2 is an exceptionally safe hashing algorithm that can be employed to hash passwords.
Though validating the credentials, the server hashes the specified password, and the hash saved in the database (for the duration of sign-up) and compares both equally of them. If the hashes match, the server then sends a ask for to the session retail outlet for the session ID.
A session shop is a medium where by facts relevant to the logged-in person is stored. It could be in memory or a databases. Redis is generally utilized as a session retailer for the reason that of its pace.
The session data includes anything linked to the person who is logged in. It could be the userId or any discipline that is one of a kind to the consumer.
This session ID is then sent again to the server, which in flip, sends the ID of the session to the customer in the variety of a cookie. Info on the consumer can then be accessed using this session ID which the retailer can question.
To log the person out, you can wipe out the cookie and delete the essential-price pair related with the session ID in the retail outlet.
Now let us acquire a look at JSON Website Tokens.
JSON Web Tokens (JWTs)
JWTs choose a wholly unique tactic to fixing the trouble. Authentication is done on the client-facet in this article, rather than in the server like in classes. The system can be illustrated in this way:
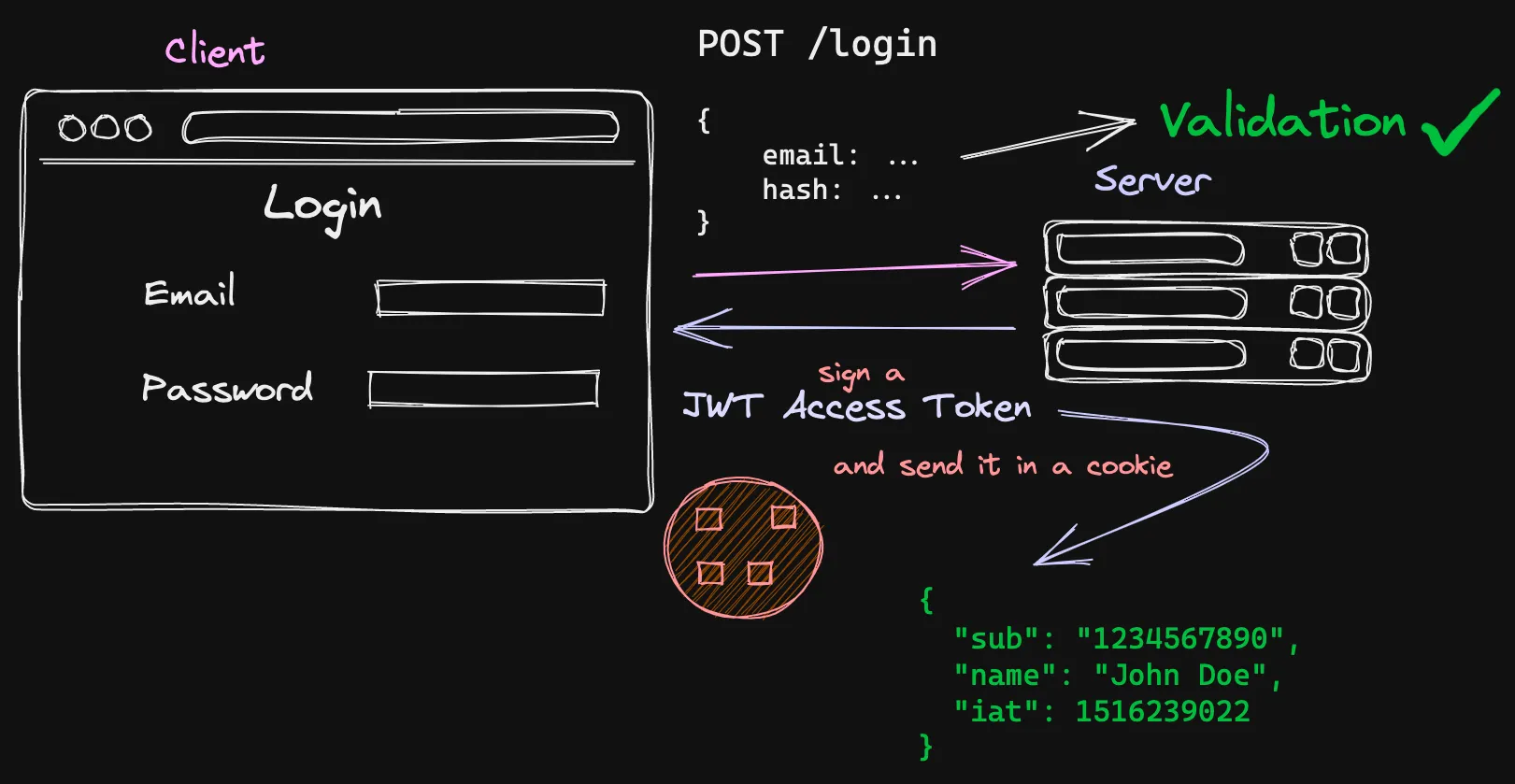
It begins the identical way as in periods, but in its place of asking the session keep for a session ID, the server issues a JWT entry token with a JWT Top secret.
This token is relayed again to the customer and ought to preferably be stored in a cookie. The JWT is not private and it need to NOT consist of private facts like the hashed password. A token should just have the user ID or other sorts of one of a kind, non-jeopardizing details.
The JWT can then be used as an Authorization Header’s Bearer Token that can be made use of to operate queries that call for auth. This JWT can be validated in the server all through requests. Since the magic formula stays personal a JWT simply cannot be forged. To log a user out, the cookie can be destroyed.
To keep the application secure, JWT tokens need to be limited-lived. Yet another token named a refresh token should be signed on login, which can renew the obtain token when it expires. When a shopper sends a request with an expired entry token, the server would use the supplied refresh token and use it to crank out a new obtain token. This way, if an attacker receives hold of an accessibility token, the validity of that token is extremely brief.
Take note: Do NOT shop JWTs in localStorage!
Storing JWTs in localStorage can make the application vulnerable to what’s known as an XSS Assault (Cross-Site Scripting).
It is a variety of code injection exactly where malicious code is injected into a site using an additional web software.
Pros and Disadvantages of employing Classes
Extra Control/Flexibility
Classes give the developer additional control about the app. If there is a breach, then you can immediately delete the session from the retail outlet, while blacklisting JWTs is difficult, and in the worst-case state of affairs, you would just have to wait for the token to expire.
Simple to Carry out
Considering the fact that session IDs are stored in cookies, there is no want to supply any request headers. This is mainly because cookies are supported instantly by browsers and all cookies are despatched as part of the ask for to all web-sites.
It also decreases bandwidth utilization when in contrast to JWT, considering the fact that there is no want to mail the token back and forth for every single request made by the customer. Cookies can also introduce a vulnerability for CSRF (Cross-Internet site Request Forgery) assaults.
This comes about when requests as a result of a destructive web site force authenticated users on other internet websites to submit a ask for to the destructive site and get entry to their credentials. This can be prevented by environment the SameSite cookie option to lax.
SameSite decides if the cookie should really be sent only to the origin site.
Stability
Session outlets are not public and are stored remotely on a server, consequently rendering the session information to be safe. In the situation of JWTs, the tokens are relayed on just about every ask for and can be intercepted. Classes are, in most conditions, safer than making use of JWTs
Scalability Challenges
Classes can be a agony to scale due to the fact there is a requirement for a spot to host the session retailer. You will need to have to keep far more facts on the retail store when a lot more people authenticate and this will choose a load on the server which can be costly depending on what internet hosting solution you go with.
Execs and Cons of making use of JWTs
Scalable
Considering the fact that JWTs store absolutely nothing on the server, it is stateless and scalable. As the consumer base grows, JWTs can scale since there is no overhead of demanding a retail outlet on the server.
You can “not-worry” about a whole lot of stuff
- CORS: Cross-Origin Source Sharing
- Area Migration
- Portability: With periods, you require a cookie retail outlet that only browsers have. You can use tokens when producing purchasers for other units much too. But then you would have to vacation resort to a distinctive place to shop the token on the shopper.
You can not certainly log a person out
You’d commonly log a consumer out by taking away the cookie with the entry token in it. But this doesn’t ensure the validity of the entry token. If an attacker will get maintain of the token, he/she can nonetheless make requests to the server and do lousy things.
To avoid these issues, you have to put into practice a blacklist method, where if you get a report of a stolen token, you increase that token to a blacklist, and any request with a blacklisted token will be blocked.
Just eradicating the token from the arms of the client does not resolve the problem. You could introduce a refresh token, but then yet again that is a different token to offer with )
They are hefty
If you store a large amount of junk on your token, you may possibly exceed the dimension limit for a cookie. And I already explained to you why storing them on localStorage is almost certainly a undesirable idea.. (CSRF wink, wink)
Stability
JWTs are basically place, not protected. They can simply be intercepted and decrypted (Actually all you have to do is paste the token into a internet site like this and you can get the consumer data inside of it). This is precisely why you ought to hardly ever retail store any sensitive details in a token.
Just store the necessary credentials that will permit the server to know who the person is. A thing basic like a userId.
Which a single should really you use?
It’s all your alternative. I desire to use classes due to the fact they are uncomplicated to implement (I really do not have to fear about refresh tokens, blacklists, etcetera.) and are additional protected (only the session ID is sent through an HTTP-Only, SameSite cookie).
I really do not uncover scalability to be an concern, especially with platforms like Railway providing a great totally free system (not sponsored!). If you have a substantial consumer foundation, and you are eager to invest a bit of revenue on a VPS or a paid cloud services, surely go with sessions.
In advance of I wrap up, here’s a record of assets that can support you with implementing auth and going a little bit deeper into the topics mentioned in this posting.
Methods
And that is it for this publish, see you on the up coming 1!

